It is important to remember that security is a journey, not a destination. No organization will ever be 100% secure, there will always be new and evolving threats. But there are things you can do to improve your organization’s cybersecurity today.
Patching
If you notice a crack in the drywall in your home, what do you do? You patch it, right? Your security system and network should be treated the same way. Every “crack” in your security system or network is an opportunity for someone with malicious intent to enter your organization. Ensuring everything is patched routinely helps to remove and prevent these “cracks” from happening. Your network and system should be patched and checked once a month. The best way to make sure this is done on time, every month, is to automate it. Humans are not reliable; they take vacations, get sick, have kids’ recitals to go to, or leave your organization. Computers will show up, every day, and do the job that needs done. I am not suggesting you rely solely on the computer automation, though. A person on your team should check periodically that the systems are getting patched appropriately and there are no causes for concern. Just like patching your drywall correctly rebuilds the strength of the wall, patching your systems correctly rebuilds the strength of your security.
Proper patching helps prevent incidents, but you also need to plan for when they happen, because they will.

Create A Plan
Every organization should have plans in place to guide them in an emergency. I’m sure you have thought about what you would do if you lost your company vehicle, are suddenly unable to receive one key component to the product you make, or your building catches fire. You have plans in place for these disasters. You should also have plans in place for when your cybersecurity is compromised. There is a lot of information you will need to have when a cyber incident takes place, and your response to the incident will go a lot smoother if you know exactly what to do and when.
The first step to building your comprehensive plan is creating an INCIDENT RESPONSE PLAN.
This plan will outline your communication steps in the beginning hours of the attack. Specifically, you will outline who to call and who makes the decisions throughout the attack, when to call in a third-party, and when to transition your focus from incident response to disaster recovery. This plan needs to be thorough, including a call tree with the contact information for who needs to be notified of the attack, an outline of who is responsible for what steps within the plan, and an exact timeline of when you will call in the third-party. You will also need to include a timeline of when you will transition to your disaster recovery plan.
A DISASTER RECOVERY PLAN helps you understand the severity of an incident to your organization through determining exactly what is at stake.

The first subject is Recovery Time Objective versus Recovery Point Objective.
Your Recovery Time Objective is the amount of time your organization can tolerate being down. The more complicated your infrastructure, the longer it will take you to recover all of your data if it is lost. If your organization is disabled by a cyberattack, would it be acceptable to you for it to take a couple weeks, or even months, to fully restore your systems to being operational?
Recovery Point Objective is how much information and data your organization can afford to lose. Are you prepared to lose that much time? How often are your backups processed? How many copies do you keep? If you only keep one copy of your backed up information, you could lose that to a cyberattack, too. How much is a day’s work worth to your organization? Two days; a week? Fully understanding the repercussions of losing weeks’ worth of data and information allows you to be prepared for the worst outcome and plan so it doesn’t happen. If your organization can’t afford to lose more than 2 days of data, back your files up every day, or multiple times a day if needed. And keep multiple copies of those backups. When an attack happens, you will be able to restore your organization exponentially quicker than if you did not have backups.
Next, you will need to identify your assets and set priorities.
In this section of the plan, you will determine the order in which your data gets restored after an attack. The most critical data your organization needs to operate will be restored first, and the less important data that is not needed for your organization to operate will be restored last. It is imperative for you to understand what your organization needs in order to get back to operational status as quickly as possible to avoid potential reputational damage. When going through the data you are backing up, annotate which data is critical, important, and unimportant. This will save you time when doing the recovery because you will be able to prioritize what gets recovered first and not have to sort through your backed up files while trying to recover from an attack.
You will also need to note who is responsible for which of your systems. Is one person specifically responsible for all critical systems, and another for important? Having this planned out ahead of time avoids chaos throughout the incident of determining who is responsible. When making these determinations, be sure to include the contact information and call list for all internal and external contacts that will need to be communicated with throughout the disaster recovery process.
You have now created multiple backups and determined who is responsible for recovering each of the systems in the event of an attack. Make certain these people understand where the backups are located and how each of them is recovered. Include detailed instructions in your disaster recovery plan to ensure the information does not get misplaced or forgotten. Also be sure your organization has enough bandwidth to download each of these backups when you need them. This may be a conversation you have with your internet service provider, and perhaps a contract they can put into place that allows you the extra bandwidth necessary when an attack happens.
The first couple hours after a disaster are critical and staff should know exactly what they are required to do to minimize damage to the organization.
You might be asking how you are going to prepare the staff to know exactly what they need to do, without having an attack on your organization.
This has a relatively simple answer: run drills.
I’m sure you run fire, tornado, and other emergency drills with your staff to prepare them for these moments. People do not think logically when they are in a state of panic, so practicing what do to in these intense situations allows them to act without very much thought when a real emergency happens. This is the same for cybersecurity. If you run drills with your staff to practice what they are to do in the instance of business email compromise, ransomware, or other attack, they will need less instruction when the actual event happens.

These drills also allow you to test your plans. If there is a step in your plan that does not work or could be better performed by someone else, drills will allow you to see those opportunities for improvement. After a drill is run, perform a lesson learned review. During this review, walk through each step of the drill and determine any weak spots in your plan and how you can make them stronger. Run drills until your plan is as optimized as you can get it, then continue to run them and check that nothing has changed over time. The first few hours of disaster recovery are absolutely critical and need to be planned out and executed perfectly for the least damage possible to your organization.
Assess Your Risk
One attempt to prevent these situations from maturing to this point is to assess the risks of your organization. I imagine you assess some risk to your organization every single day. What happens if a widget breaks, or if a person suddenly leaves for another job. You probably have plans for those risks if they were to happen. To plan for cybersecurity risks, you should put a dollar value to all systems and data within your organization. Having a dollar amount assigned to these things helps to determine if the cost of protecting each asset is worth the value of that asset. This goes deeper than intentional attacks, too. Determine the risk of an employee accidentally deleting all of your data with a simple click of the wrong button. Attacks are not the only risks to your organization’s cybersecurity; you need to assess all risks, internal, external, and natural to be fully prepared.
Assess and Improve Your Cyber Posture
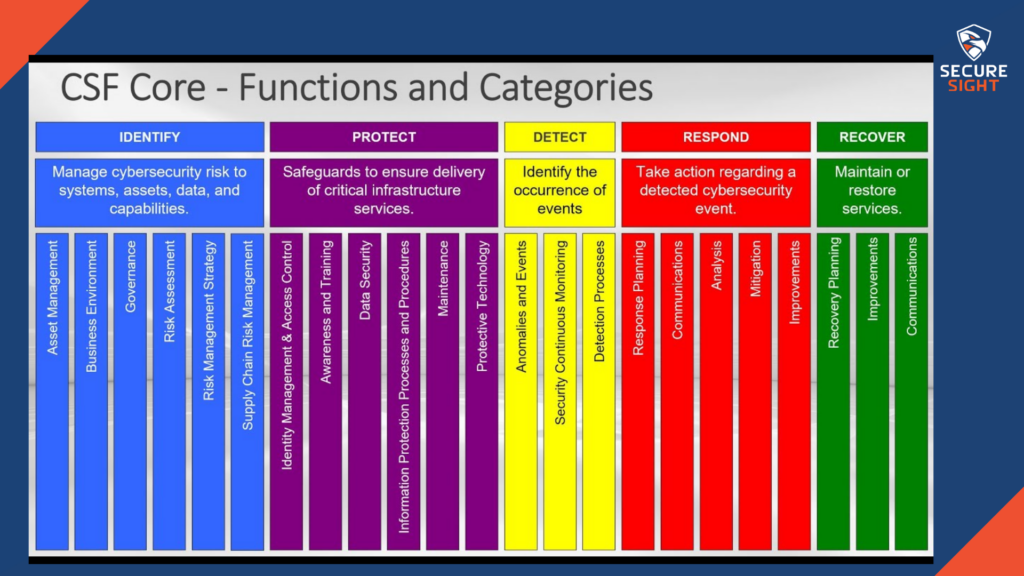
There are different categories within your organization’s overall cyber posture. They are identify, protect, detect, respond, and recover.
Identify
Identify your assets, risks, and threats. Most organizations don’t know exactly what they have as assets and the monetary value for them. Determine which of your assets are worth protecting based on their value. Risks to your organization are not only intentional attacks performed by malicious hackers. Does your receptionist have access to sensitive financial information for your customers? It that access necessary to perform their job? If not, having access allows one more potential risk for your organization to lose information. And lastly, determine the threats to your organization. Figure out who would want access to your data for malicious intent. If the information and data wasn’t valuable, you wouldn’t be protecting it.
Protect
Add controls to your systems to keep their security up to standard. Look into implementing an Endpoint Detection and Response (EDR) software to replace the traditional antivirus software. Antivirus does not protect against behavioral based threats, EDR evaluates the data on your network and systems to determine a baseline of “normal” and flags anything that falls outside of that baseline as potentially harmful. Other systems you can implement to better protect your organization are firewalls, spam filters, password vaults, 2 Factor Authentication, and security awareness training to your staff. You can also apply the principle of least privilege to your organization when necessary. Sometimes the best option is to minimize the material impact rather than trying to recover everything.
Detect
The most important part to keeping your organization secure is the quick detection of potential threats. Your organization should have continuous security monitoring to check on the tools you have in place. Just like keeping your car serviced every few months, you want to maintain your security systems to keep them running efficiently. Continuously monitor and check your tools and controls within your systems to ensure they are meeting the standards of security for your organization. Detecting potential threats is the most important part of this cybersecurity framework, this is what determines the level of impact your organization will face as the result of an attack. Having the goal to prevent all attacks before they happen is unattainable. You cannot prevent all attacks. Your goal should be to discover problems before they cause material impact on your organization.
Respond
Planning ahead of time for the worst-case scenarios allows your staff to respond to an incident in the most efficient way possible. Create documents that walk your staff through the steps to mitigate the risk as much as possible and run drills to check the validity of these plans. Ask your cybersecurity provider or internal staff for an in-depth Incident Response plan and be sure it includes at what point the incident is no longer containable for them and who they will need to contact at that point for assistance.
Be Your Own Advocate
The hard truth is, no one will care about your organization as much as you do. You will have to be your own advocate in some situations. It is a good practice to ask questions and do your own research before committing to a cybersecurity plan; make sure you are getting what is necessary for your organization. Don’t assume you’re covered because you have a few checkpoints in place against attacks. You can never be too protected. For example, The United States Marshal Services was recently the victim to a ransomware attack. They have a cybersecurity budget of $11 billion per year, showing even the largest of cybersecurity budgets do not prevent every single attack. There is no existing software that fully prevents cyberattacks, and there is nothing to suggest this software will be created soon. Create a budget to protect your organization from multiple angles with different available tools. This is not a problem that is going to go away.

