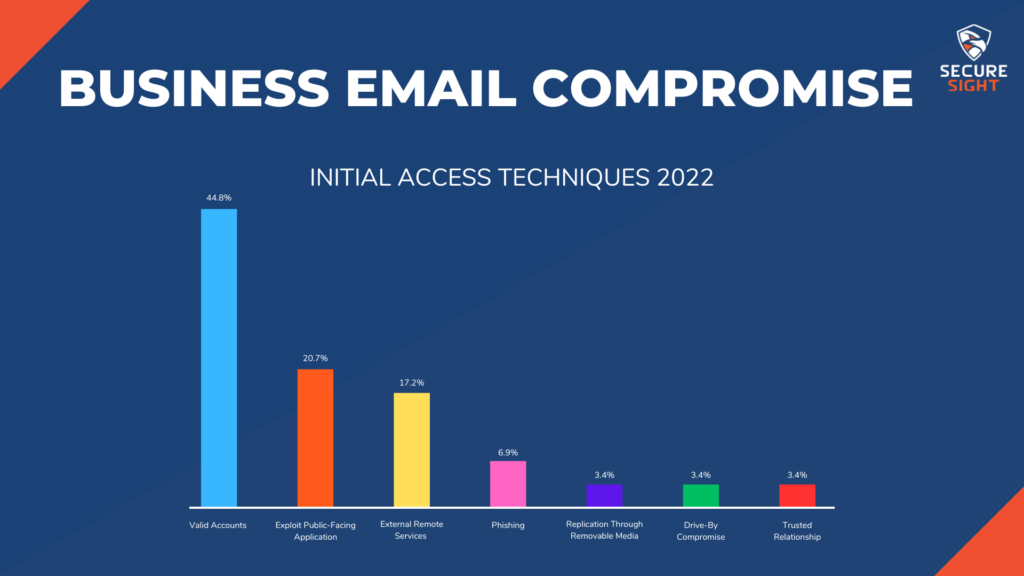
Now that your mental image of a hacker has been adjusted away from the media portrayal and we’ve gone over how they operate on a general level, let’s get into some specifics. The first step to a cybercrime is finding an entry point into your organization, and from there hackers are able to cause a magnitude of material impact.
The industrialization of the cybercrime economy is creating lower skill barriers for entry by providing greater access to tools and infrastructure needed for an attack. In other words, the cybercrime economy is creating a “cybercrime for dummies” resource, allowing almost anyone to enter the business. This is causing the number and frequency of cybercrimes to continually rise. Cybercriminals are even collaborating across time zones and language barriers. They are realizing that just like in other industries, cybercrime is more profitable when working together.
Throughout 2022, SecureSight helped our clients with a multitude of different incidents. We helped them handle everything from business email compromise to ransomware attacks to data breaches. The Cybersecurity industry is ever-changing and responding to these incidents allow us to collect data and gain insight into the cyberthreat landscape of the local community. I would like to share a couple examples with you of incidents that we helped resolve locally. Incidents like these are happening to your peers and companies that you may be partnered with.
An Example of Business Email Compromise
A C-level executive from a production plant received a call from their local bank. There was an attempt made to wire $2,000,000 to another company’s bank account for the purchase of a new piece of equipment. This was not an unusual transaction against this company’s account authorized by this executive. However, when the banker attempted to send the wire, it was returned with an error stating “incorrect account number.” This error required the banker to call the recipient and confirm the account information. It was discovered that the number provided was not even close to the recipient’s correct account number. The banker then called the C-level executive and found that he was unaware of an email that had been sent to the bank stating to change the recipient’s account information.
After this phone call, the bank immediately froze all assets and services for the company until an audit was performed. This organization is dealing with a Business Email Compromise attack and needs to be sure the attacker has been stopped before any funds are released.
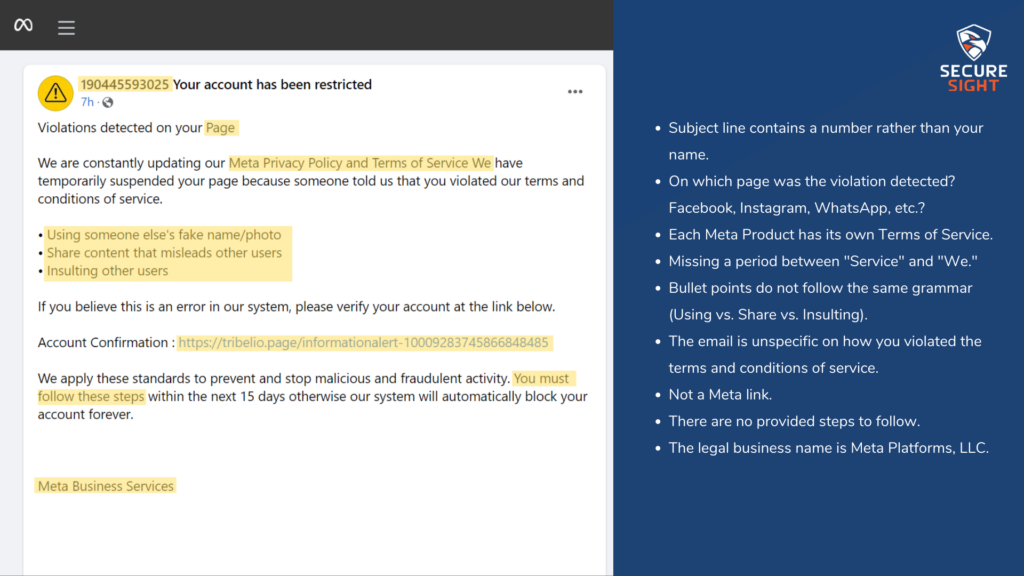
You’ve all seen these emails.
They are sometimes poorly written and usually ask about an invoice you didn’t pay or tell you that your computer has been hacked and your inappropriate pictures will be released if you don’t pay them in Bitcoin. When you see them, you probably ask yourself how people actually fall for these scams. Many of these attacks are more sophisticated versions of those emails.
In this example, it was discovered the attacker had been logged into the executive’s email for over 4 months, waiting for the perfect opportunity to come along before risking exposure. The equipment purchase authorized by this executive was exactly the opportunity they had been waiting for.
Once the payment had been authorized by the executive, the attacker created rules within their inbox to direct any communication about this transaction to an outside email address. These rules allowed the communication to be forwarded to the hacker and stay hidden from the executive. Through perfectly written emails, the attacker convinced the bank in just 3 days to change the account information for the recipient of the payment.
All without alerting the executive of the communication that was happening.
You may be wondering why the bank wasn’t suspicious of the outside email account where the emails were being forwarded. The attacker had used the account of another local organization that had previously done business with. After looking through the executive’s emails, the original phishing email was found, looking to be from the other local organization, asking about an invoice.
Had the banker not received the error about the incorrect routing number, this production plant would have lost $2,000,000 in one attack. Thankfully, the attacker made a critical mistake in the routing number that allowed them to be exposed and stopped.
This example helps stress the very key point in this topic, which is:
Cybersecurity is a team sport we all have to play.
The email that got sent from your account may have only resulted in you having to send the embarrassing follow-up communication to everyone letting them know you had been hacked and not to open the email if they received it. You’re surprised someone was able to guess your password, “Fluffy1981” so you change it to “Fluffy1981!” and move along with your day.

While this compromise did not result in any major damages for you, Business Email Compromise cost U.S. companies $2.4 billion in 2021.
BEC is the costliest method of cyberattacks and accounts for 59% of the total cost from the top 5 crime losses globally.
This statistic only represents the payments that get caught and reported to the FBI; think about the number of payments that are not caught and reported.
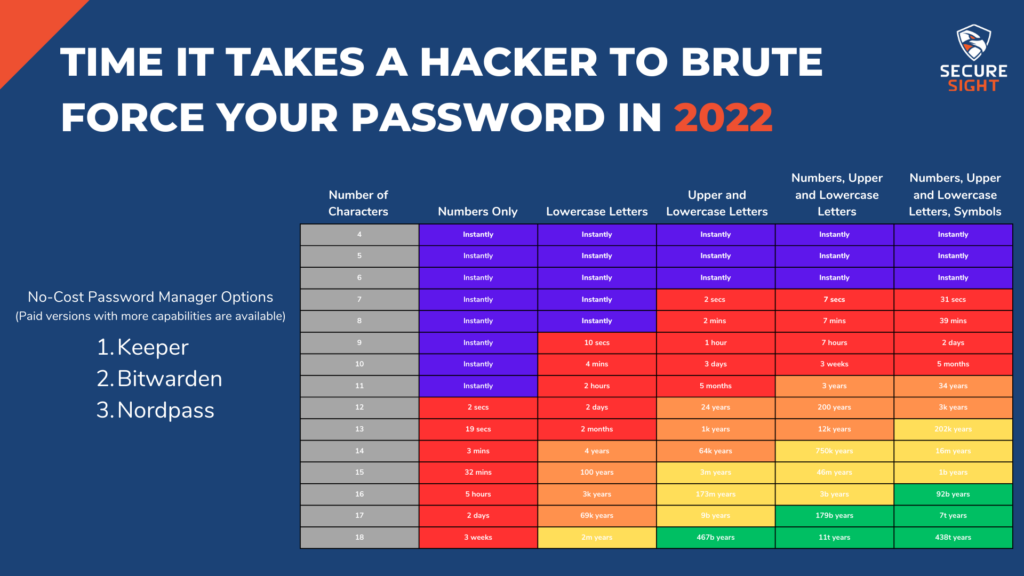
Fighting BEC is complex. While email spam filters help with this problem, they will never prevent all malicious emails from reaching your users. Luckily, there is a simple, albeit inconvenient, guard that can be implemented at almost no cost to your business. 2 Factor Authentication. If you are not familiar with this, it’s a secondary product that provides additional security through sending a code or requiring a second device in order for the user to log into their account. This additional step in the login process prevents 99% of email credential attacks, making BEC not worth the attacker’s time to continue pursuing at your company. For attackers, time is money, so if they are not able to access the email account immediately, they will move onto their next target. Microsoft and Google both offer 2FA apps that can be used on email accounts hosted on their services and other services such as Facebook and LinkedIn.
2FA is not an option for every account, though. For those that do not offer this extra protection, using a password manager will significantly lower the possibility of your credentials being attacked. For only a few dollars per month, you can subscribe to a cloud-based password manager that will sync to all of your devices. If this is out of budget, there are also open-sourced password managers that are offered for free. You can host these yourself, but they are not as convenient as a cloud-based option and require extra steps to backup and protect the database.
Some examples of free password management programs with available paid versions are Keeper, Bitwarden, and Nordpass.
But wait!
You tell me you have different passwords for most of your accounts!
They are stored in a binder in your top desk drawer, or you use the offered storage by Google Chrome.
Storing passwords in a browser or in a physical location is a major security risk. Browsers may have vulnerabilities that allow hackers to extract saved passwords, and physical storage is susceptible to theft, loss, or duplication. Using a password manager is a safer alternative. Password managers securely store and encrypt your passwords, making it more difficult for hackers to obtain them. Additionally, password managers can create passwords for each new account that is added to your vault. By using the suggested password, you are ensuring strong and unique passwords for each account, and you don’t have to worry about memorizing any of them! Using strong and unique passwords for each account is crucial to prevent unauthorized access to your sensitive information.
The problem with BEC is that, although the monetary impact to businesses is large, it’s an uninteresting topic. Whether someone sent out a payment of $50 or $50,000,000 is irrelevant, no one outside of the business and business owners are impacted. In our next post, we’ll be talking about something more interesting: the reason most business owners are kept up at night. Can you guess what that is?