In the first half of 2022, there were an estimated 236.1 million ransomware attacks globally.
Here’s an example of how a ransomware attack could progress.
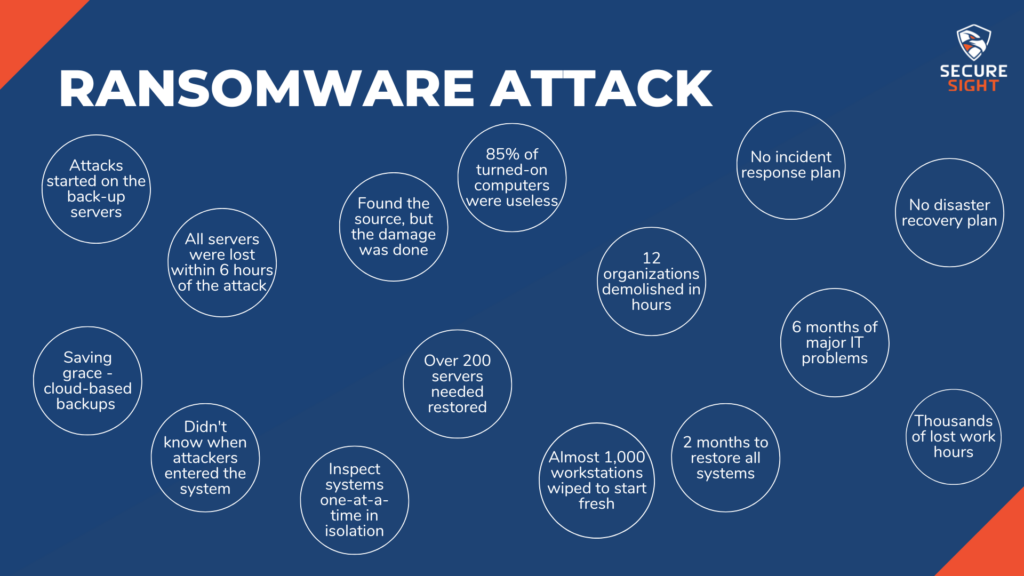
An organization was about 6 hours into a ransomware incident. The attackers started on the backup servers that were located at another site, provided by this organization’s internet service provider. From here, the attackers were able to spread the ransomware to all of the organization’s servers. By the 6-hour mark, the organization had lost all their servers and the ransomware was spreading through individual workstations.
This is not a solo organization, though.
This is an organization connected to many others throughout the area. The ransomware was able to maneuver through these connections and infect a total of 12 entities. All starting through one organization’s backup servers.
Due to having connections with so many others in the area, this organization had a strict 24/7 operating requirement. They were not able to shut down their systems in attempt to stop this attack. At this point in the incident, the critical systems had not been compromised and were still fully functioning, thankfully. There was no way of knowing how long that would last, though.
85% of computers that were turned on were useless to the employees.
Because the attacks started from the backup servers, those were useless as well. Even though most servers were encrypted, the infection continued to spread like the plague.
12 organizations were crippled within just a few hours of the attack.
The organization decided it was time to ask for assistance from a third-party. Once they were involved, it only took about 4 additional hours to find the source of the attack and stop the spread. This was almost 12 hours in, though. Most of the damage had already been done. The third-party advised the organization that the next step was to talk with IT staff and management to decide on what their plan was moving forward with disaster recovery. Unfortunately, there was no plan. Management had not thought at all about what they would do if something like this were to happen.
There was one saving grace.
Two months prior to the attack, the main organization had implemented cloud-based immutable backups for all their servers. This is a backup file that cannot be altered in any way. The organization had a restore point, but there were no logs indicating a breach in any of the systems. This caused a problem when trying to determine which backed up version to restore because no one knew when the attackers had first entered the systems. To determine which backups to use for each system, the third-party decided the best course of action was to turn them on in isolation one at a time. This allowed them to do a thorough inspection to determine if the system had been compromised at the time that specific backup was uploaded. This made the restore process take considerably longer. Over 200 servers needed to be restored to a production state, and almost a thousand more workstations needed to be completely wiped. This process took about 2 months. Even once all systems were restored, the on-site IT staff spent the next 6 months troubleshooting major problems at each of the connected organizations. Overall, this attack caused thousands of hours’ worth of work to be lost.
How does something like this happen?
Even if this organization had the best IT staff and equipment available, if any of those systems were misconfigured, it allowed a vulnerability for attackers to exploit. In this example, the organization did have a very experienced IT staff and an extremely popular security software that claimed ransomware could not be executed on its systems. However, after the organization paid the vendor to install the equipment, they did not do anything to further service the systems. While these tools were very capable of keeping this organization secure, they had been out-of-date, so were not as effective against attacks.
For this example, the attackers used a well-known vulnerability within an unpatched system to enter the network. Once they were inside, they could do whatever they wanted with little to no effort because the tools weren’t configured properly and were not monitored. There were many alerts within the security tools in place. Had these tools been monitored by a skilled professional, the alerts would have been caught and this attack could have likely been stopped before it became a ransomware situation. Instead, the 12 organizations were brought to their knees by attackers looking for a $5,000,000 payment.
But wait, there’s more!
There was also serious reputational damage caused to the organization from which the attack originated. No one in management had acknowledged that an attack like this was possible, and there were no plans or policies in place for when an attack like this did happen. Due to this lack of preparation, the employees were panicking. One employee of the affected organizations called the media and the FBI. Another employee went so far as to take a couple computers from the organization and turned them over to the FBI for inspection.

Now, I want to be clear…
Through this example, I am not suggesting working with the authorities is a bad thing or that an organization should try to cover up an attack. However, disclosure should be done in a responsible manner, controlled by leadership and with the help of legal counsel. The employees taking these matters into their own hands caused the media to be misinformed, which led to damaging and inaccurate statements being published.